Keep Sensitive Data Safe with Continuous Compliance
Continuous Compliance from Perforce Delphix identifies sensitive information and masks data in non-production environments used for development, testing, analytics, and artificial intelligence (AI). With fast, automated, AI-powered masking, enterprises mitigate cybersecurity risks and stay compliant with privacy and industry laws.
The Perforce Delphix Difference: Continuous Compliance
Key Capabilities of Continuous Compliance
Mask a broad range of data sources including RDBMS databases, NoSQL, mainframe, data warehouses, and file systems.
- Mask across private, public hybrid, and multicloud environments.
- Support all clouds including PaaS, cloud-native databases, and object storage.
- Preserve referential integrity across heterogeneous sources.

Deploy Continuous Compliance and immediately mask data without requiring specialized programming expertise or lengthy, expensive service engagements.
- API or user interface (UI) based setup.
- No-code/low-code solution.
- Synthetic data generation using AI.
- Sensitive data discovery templates for specific apps and regulations.
- Out-of-the-box and customizable masking algorithms.

Continuous Compliance algorithms mask data consistently to preserve referential integrity, keeping important data relationships intact for accurate analysis and integration testing.
- Ensure consistently masked values within and across systems.
- Maintain referential integrity even across hybrid or multicloud architectures.

Continuous Compliance seamlessly integrates with Delphix Continuous Data to combine masking with advanced data virtualization. Instantly deliver masked, virtual data copies to non-production environments.
- Enable fast, self-service access to masked datasets.
- Eliminate data delivery bottlenecks for DevOps, continuous integration/continuous deployment (CI/CD), test data management, and AI workflows.
- Reduce costs with space-efficient, virtual data copies.

How Continuous Compliance Works
Define Compliance Policies
Define a consistent set of compliance policies for laws such as GDPR. Easily determine what data values are masked, when, where, and how.
- Use wizard-driven rule creation.
- Define policy once and deploy anywhere.
- Audit and report against policy enforcement.
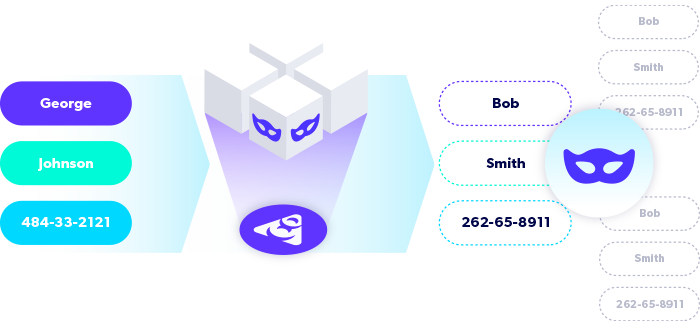
Identify & Mask Sensitive Data
Automatically discover sensitive information across a broad range of data sources. Masking replaces sensitive data with fictitious data while maintaining referential integrity.
- Identify personally identifiable information (PII) or protected healthcare information (PHI) such as names, email addresses, and payment information.
- Use irreversible masking algorithms or tokenization to desensitize data.
- Generate synthetic data values using Delphix AI.
- Retain data realism to preserve value for development, testing, analytics, and AI.

Use Compliant Data
Deliver virtualized, masked, and synthetic data copies to downstream environments. The combination of masking, virtualization, and synthetic data generation enables teams to accelerate compliant data delivery to developers, testers, and data scientists.
- Provide self-service access to compliant datasets.
- Refresh or rewind datasets after masking jobs or test runs.
- Reduce storage requirements by using space-efficient virtual data.
Protect Sensitive Data Across the Enterprise
Delphix Continuous Compliance supports the data sources that enterprises depend on for their most important initiatives.
- Mask databases, data warehouses, and files.
- Work in any cloud environment.

Delphix Continuous Compliance FAQs
Learn more about Delphix Continuous Compliance.
Delphix Continuous Compliance automatically identifies and masks sensitive data values in environments for development, testing, analytics, and AI. This helps enterprises mitigate the risk of cyberattacks while enabling compliance with privacy and industry laws such as GDPR, FINRA, CCPA, HIPAA, and PCI DSS.
Delphix Continuous Compliance scans data sources to identify fields with sensitive data including names, email addresses, and payment information. Continuous Compliance transforms those sensitive values into realistic, yet fictitious values to eliminate privacy risks while preserving the value of the data.
Delphix data masking neutralizes data risk in non-production environments, stripping data in those environments of sensitive values that should not be exposed internally or externally. This mitigates the risk of data breach or exfiltration and enables compliance with privacy laws.
Delphix provides static data masking (or persistent data masking) that irreversibly transforms sensitive data at rest in the targeted source.
Continuous Data is the Perforce Delphix product that provides data virtualization capabilities. It seamlessly integrates with Continuous Compliance.
See Delphix Continuous Compliance for Yourself
Get a no-pressure walkthrough from one of our product specialists. You’ll learn how Delphix Continuous Compliance:
- Helps you easily create compliance policies.
- Finds sensitive data automatically.
- Applies advanced masking algorithms.

