Achieve Compliance with Stringent Privacy Laws
Regional privacy policies — including GDPR, FINRA, CCPA, and GLBA — are constantly evolving with compliance changes. Industry regulations such as PCI DSS and HIPAA are increasingly stringent. Perforce Delphix helps businesses achieve compliance with these laws by enabling them to assess data risk, mask sensitive information, generate synthetic data using AI, and control who accesses what data, when, and how.
Mitigate Risk with Data Compliance Solutions
Adopt a Comprehensive Approach with Delphix
Delphix Continuous Compliance is a foundational part of the Delphix DevOps Data Platform, enabling teams to build a compliant data layer with data masking.
With automated data discovery, advanced masking algorithms, and an intuitive interface for defining and deploying masking policies, Continuous Compliance offers a comprehensive approach to mitigating risk in the non-production environments where most sensitive data resides.
Continuous Compliance seamlessly integrates with Delphix Continuous Data to deliver virtual copies of masked datasets. Together, masking and virtualization bring safety — and speed — to data vital for development, testing, and AI.

Delphix Compliance Services accelerates data compliance for Azure Analytics and AI, delivering compliant, quality data at high speeds.
With sensitive data discovery and masking using Azure-native ETL frameworks, Delphix Compliance Services brings compliance to key data stores such as Snowflake, Databricks, Azure Data Lake, and Azure SQL Server Data Warehouse.
Enable analytics and data science teams to deliver accurate and timely insights to the business, without exposing the organization to regulatory and data theft risks.

Businesses that must adhere to privacy laws use Delphix Data Control Tower as a single point of control for compliance, enabling them to gain full visibility of sensitive data and centrally control risks in non-production environments.
- Sensitive data heatmap and masking logs for development, testing, software reliability engineering (SRE), and artificial intelligence (AI) environments.
- Centralized governance for data with a data library and data tagging.
- Tag-enabled role-based access controls and integration with authentication systems such as Active Directory and Okta.

Hyperscale Compliance provides ultra-fast masking for large, complex datasets enabling compliant data delivery for DevOps, continuous integration/continuous deployment (CI/CD), test data management, analytics, and AI initiatives.
Large, growing datasets can take days or weeks to mask through traditional batch processes, preventing teams from meeting delivery timeframes and delaying critical projects.
By parallelizing masking jobs across multiple streams, Hyperscale Compliance achieves 10x masking speeds for massive data volumes, unblocking innovation.

How Data Compliance Solutions Work
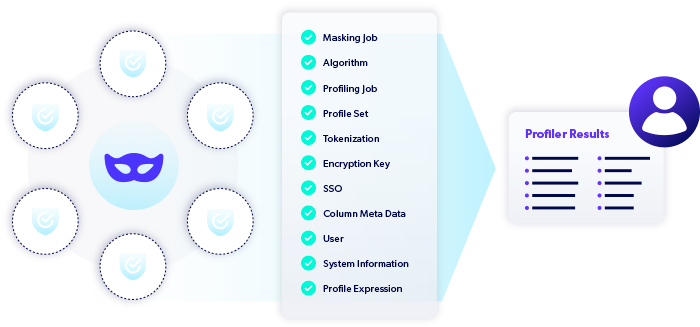
Define Compliance Policies
Define and enforce a consistent set of compliance policies for industry and data privacy regulations. Easily determine how sensitive data values are masked, as well as who has access to what data environments, when, and where.
- Use a wizard-driven rule creation system for defining masking policies.
- Define policy once and deploy it across clouds, applications, and geographies.
- Audit and report against policy enforcement.
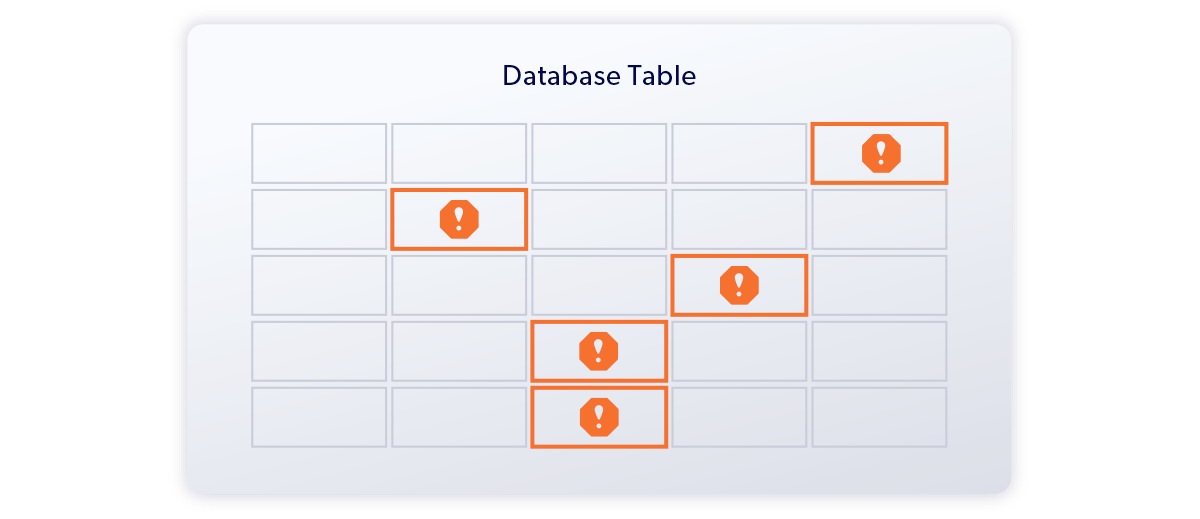
Identify and Protect Sensitive Information
Identify sensitive information such as names, email addresses, and credit card numbers for compliance policies. Protect data by transforming sensitive data values into synthetic yet fictitious values.
- Use out-of-the box discovery sets for specific regulations and packaged applications.
- Maintain an enterprise-wide sensitive data heatmap.
- Mask data across a range of data sources including relational databases, data warehouses, and files.
- Generate synthetic data using an optional AI model.
- Preserve referential integrity across datasets and clouds.

Deliver and Govern Data
Integrate data masking, synthetic data, and data virtualization to automate the delivery of virtual, secure data copies into non-production environments. Govern environments by cataloging datasets and controlling who has access.
- Build a library of virtual datasets for development, testing, analytics, and AI.
- Apply tags and role-based access controls.
- Provide universal reporting and insights across non-production.
Meet Compliance Regulations With Data Compliance Solutions
GDPR
The General Data Protection Regulation (GDPR) is a legal framework requiring businesses to protect the personal data and privacy of European Union citizens.
CCPA
The California Consumer Privacy Act (CCPA) gives California residents control over how businesses collect, use, and share their personal information.
FINRA
The Financial Industry Regulatory Authority (FINRA) in the U.S. regulates broker dealers and exchange markets to protect investors.
LGPD
Brazil’s Lei Geral de Proteção de Dados (or LGPD) regulates how any organization doing business in Brazil protects the personal information of its citizens.
POPIA
The Protection of Personal Information Act (POPIA) is a South African law that protects the privacy of citizens and governs how personal information is processed.
DORA
The Digital Operational Resilience Act (DORA) is a European Union (EU) regulation that aims to strengthen the financial sector's information and communication technology (ICT) security.
Saudi Arabia PDPL
The Saudi Arabian Personal Data Protection Law (PDPL) sets privacy standards for companies that collect, process, disclose, and retain personal data.
HIPAA
The Health Insurance Portability and Accountability Act (HIPAA) is a US law that establishes standards to protect sensitive health information.
GLBA
GLBA stands for the Gramm-Leach-Bliley Act, a law that requires US financial institutions to protect consumers' non-public personal information.
PCI DSS
PCI DSS, or Payment Card Industry Data Security Standard, is a set of rules that protect credit card and debit card information from fraud and theft.
Data Compliance Solution FAQs
Learn more about Delphix data compliance solutions.
Data compliance solutions mitigate regulatory and security risks by giving businesses a systematic approach to understanding, monitoring, transferring, controlling, securing, or reporting against their data — particularly personal or confidential data.
Data compliance solutions reduce the risk of security incidents and ensure businesses adhere to increasingly stringent privacy and industry laws. Regulatory non-compliance can result in fines, reputational damage, and even jail time.
Modern enterprises utilize a variety of data compliance solutions including software for data discovery, data masking, data backup and recovery, data governance, identity access and management, and risk management.
Contact the Delphix team if you have questions about which data compliance regulations we can help you with.
See Delphix for Yourself
Request a no-pressure demo today. Get answers to your questions and find out how Delphix will help you achieve compliance, speed, and quality — without any trade-offs.
Explore the Delphix Platform
Learn more about how Delphix delivers, masks, and controls data for the enterprise.
