Close Critical Data Protection Gaps
Perforce Delphix brings resiliency to your most important enterprise applications. Gain continuous data protection for ransomware costs and downtime, deleted data, and other types of data loss. Find and mask sensitive data to safeguard against data breaches and exfiltration.
Protect Your Most Important Enterprise Applications and Data
Key Products
Delphix Continuous Vault delivers a continuous data protection solution to mitigate cyberattack risks.
In a downtime event such as a ransomware attack, your organization needs to rebuild applications and data quickly to a known good state.
Continuous Vault uses data virtualization to immutably protect and recover data to any point in time down to the second or transaction. And with API automation, teams can swiftly rebuild full application stacks to get mission-critical systems back online.

Delphix Continuous Compliance enables your teams to build a compliant data layer with data masking.
Continuous Compliance offers a comprehensive approach to mitigating privacy and exfiltration risks in the non-production environments with:
- Automated sensitive data discovery.
- Advanced masking algorithms.
- An intuitive interface for defining and deploying masking policies.

Deploy a comprehensive, fully engineered data protection solution through Dell and Delphix. With Delphix software running on Dell infrastructure, your enterprise can quickly and automatically recover multiple applications to a consistent data state.
- Get "Rapid Recovery in a Box” from Dell and Delphix.
- Gain a fully engineered solution includes data protection software on hyper-converged infrastructure.
- Protect enterprise apps while reducing administrative cost and complexity.

How Delphix Data Protection Solutions Work
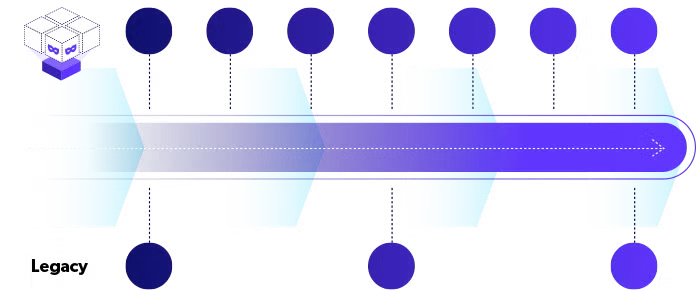
Provide Continuous Data Protection
Delphix connects to enterprise applications with the ability to continuously capture change data from sources down to the second or transaction.
- Ensure non-disruptive sync with data sources.
- Store data in an immutable vault with the ability to lock retention and policies.
- Preserve a more granular data history than backup solutions; Delphix provides near-zero RPO.
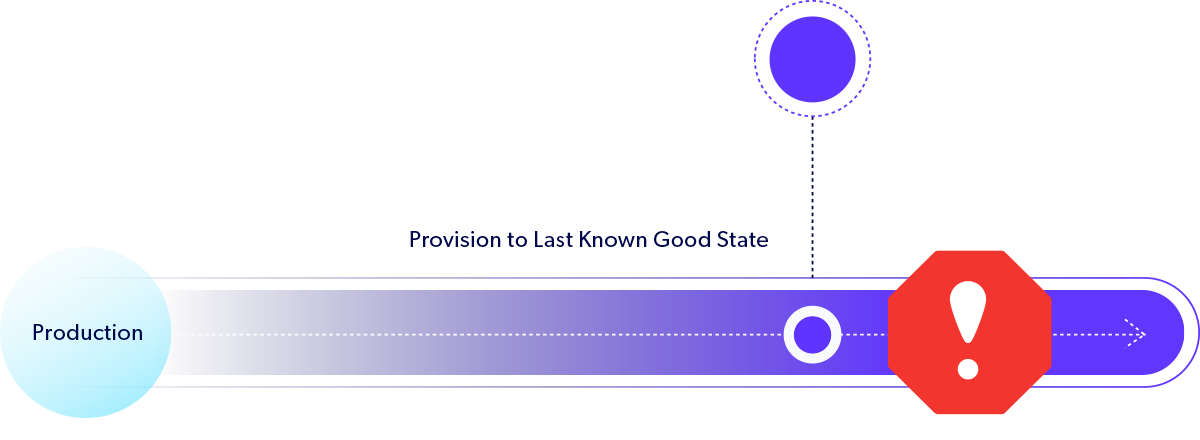
Enable Fast, Efficient Data Recovery
With Delphix, teams recover from clean state — a point just prior to an attack, in just minutes. In contrast, businesses can lose an entire day of data recovering from yesterday’s backup. On top of that, the recovery time from full and incremental backups can take another day — resulting in a 2-day recovery window. That’s not the case with Delphix.
- Rapid recovery with 100x RTO/RPO advantage over traditional backups.
- Integrated recovery restores multiple applications to a consistent state, leveraging database cloning to
enable recovery point creation and testing of backup procedures. - Simultaneous recovery from multiple points in time to quickly identify last known good state.
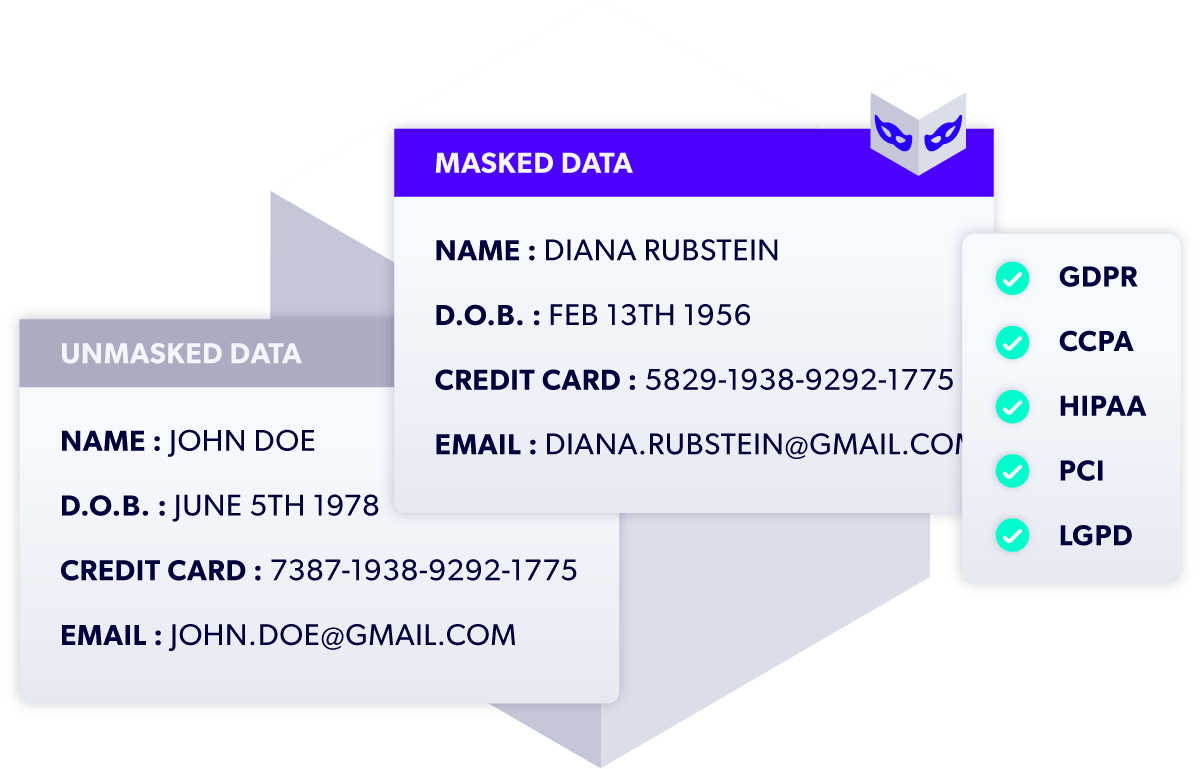
Find and Mask Sensitive Data
Mask sensitive data in environments for development, testing, analytics, and artificial intelligence (AI) to shrink the surface area of risk for exfiltration and extortionware.
- Discover sensitive data automatically, including names, email addresses, and payment information.
- Mask data by transforming sensitive values into realistic, yet fictitious values.
See Delphix for Yourself
Request a no-pressure demo today. Get answers to your questions and find out how Delphix will help you achieve compliance, speed, and quality — without any trade-offs.
Explore the Delphix Platform
Learn more about how Delphix delivers, masks, and controls data for the enterprise.
